Hacker Group Akira Threatens: Unveiling Their Sinister Plans And Implications
Hacker Group Akira Threatens: The emergence of a new ransomware strain attributed to the notorious hacker group known as Akira has sent shockwaves through the cybersecurity community. With their distinct characteristics and relentless targeting of organizations in various sectors, Akira poses a significant threat to businesses worldwide. In this article, we delve into the menacing tactics employed by Akira, exploring their data collection methods and ransom demands that include exposing victims’ sensitive financial information. Stay informed about this cybercriminal group’s activities and discover how to protect your organization from their malicious attacks on esportscampus.vn.
I. Akira Ransomware: Emergence and Unique Characteristics
The Akira ransomware, named after the renowned cyberpunk manga and movie from the 1980s, is a recent addition to the arsenal of hacker group Akira. This new variant of ransomware first surfaced in March 2023 and has gained attention not only for its resemblance to its namesake but also due to its distinct characteristics compared to the previous version that emerged in 2017.
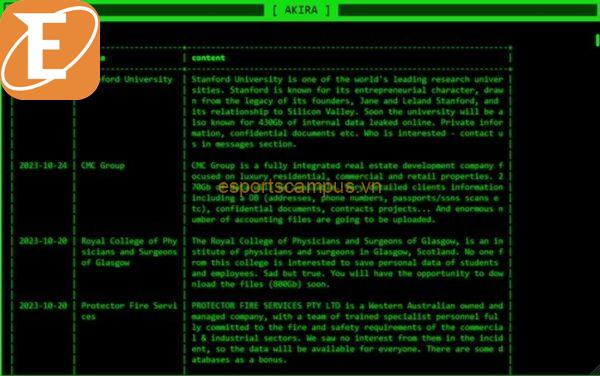
One of the standout features of this new iteration is its indiscriminate choice of targets. Akira has targeted a wide range of organizations spanning various sectors, including financial institutions, real estate companies, manufacturing firms, and even day-care centers. Unlike many cybercriminal groups that prioritize attacking large organizations with substantial resources, Akira has shown no hesitation in targeting smaller entities as well.
II. Targets and Strategies of the Akira Hacker Group
The Akira hacker group, utilizing the newly identified Akira ransomware, has strategically targeted a diverse range of organizations, including those in the financial, real estate, manufacturing sectors, and even day-care centers. This cybercriminal collective’s modus operandi is unique, transcending traditional boundaries and displaying a keen interest in both large-scale enterprises and smaller entities.
The hacker group’s selection of targets appears indiscriminate, suggesting a pragmatic approach rather than a specific focus on high-profile organizations. This inclusivity encompasses a variety of sectors, raising questions about whether the choice of victims is driven by opportunity rather than a deliberate targeting strategy. The inclusion of day-care centers, for instance, indicates a potential lack of discrimination in their victim selection process.
Prior to initiating the encryption process, the Akira hackers systematically gather sensitive information from the networks of the targeted companies. This meticulous approach involves extracting financial data, including bank reports, income details, savings, and investment information. The subsequent ransom demands leverage this acquired information, with threats to expose such financial intricacies if negotiations fail. This tactic underscores the hackers’ intent not only to encrypt data but also to exploit the fear of reputational and financial damage.
III. The Consequences of Non-Negotiation and Post-Payment Security Report
Threats of Exposing Financial Information
Akira’s tactics go beyond encrypting data and demanding ransom payments. They employ a sophisticated strategy that involves threatening to expose sensitive financial information if victims refuse to negotiate. The cybercriminals unabashedly claim that they have access to bank reports, income, savings, and investments, and they use this information as leverage to coerce organizations into compliance. By playing on the fear of reputational damage and regulatory repercussions, Akira aims to push victims into engaging in negotiations. The consequences of non-negotiation can be severe, with the potential release of confidential financial data that could have far-reaching consequences for both individuals and organizations.
The Post-Payment Security Report: Revealing Vulnerabilities
One of the unique aspects of Akira’s ransomware operations is their promise to provide a post-payment security report. This report claims to disclose the vulnerabilities that were exploited during the attack. While it may seem counterintuitive to provide such information, the cybercriminals position it as an opportunity for victims to assess and rectify their system’s security weaknesses. By offering this exclusive insight, Akira aims to present themselves as not only capable adversaries but also as potential allies in securing their victims’ networks. However, it is crucial to approach this offer with caution, as there is no guarantee of the report’s accuracy or if it will indeed be provided. Organizations should prioritize consulting with cybersecurity s and implementing robust preventative measures instead of relying solely on the promises made by cybercriminals.
IV. Conclusion
In conclusion, the hacker group Akira has emerged as a formidable threat with their new ransomware variant. Their unique approach to targeting organizations across various sectors, indiscriminately exploiting vulnerabilities, is a cause for concern. The group’s tactics of collecting sensitive financial information and using it as leverage in the negotiation process reveals a disturbing level of sophistication. Moreover, the promise of providing a post-payment security report poses an additional risk for victims.
It is crucial for organizations to remain vigilant and implement robust cybersecurity measures to protect themselves against threats like Akira. Regular system updates, strong passwords, employee training on recognizing phishing attempts, and regular data backups should be enforced to minimize the impact of ransomware attacks. Additionally, collaboration between law enforcement agencies and cybersecurity s is essential in tracking down and apprehending these cybercriminals.